
by Cyver | Feb 7, 2024 | New Features
For many of our clients, Cyver Core is the primary tool you have for managing clients, incoming work, and pentests. That often means having anywhere from a few to hundreds of clients in the platform, complete with their teams, their pentests, and all their assets....
by Cyver | Oct 4, 2023 | New Features
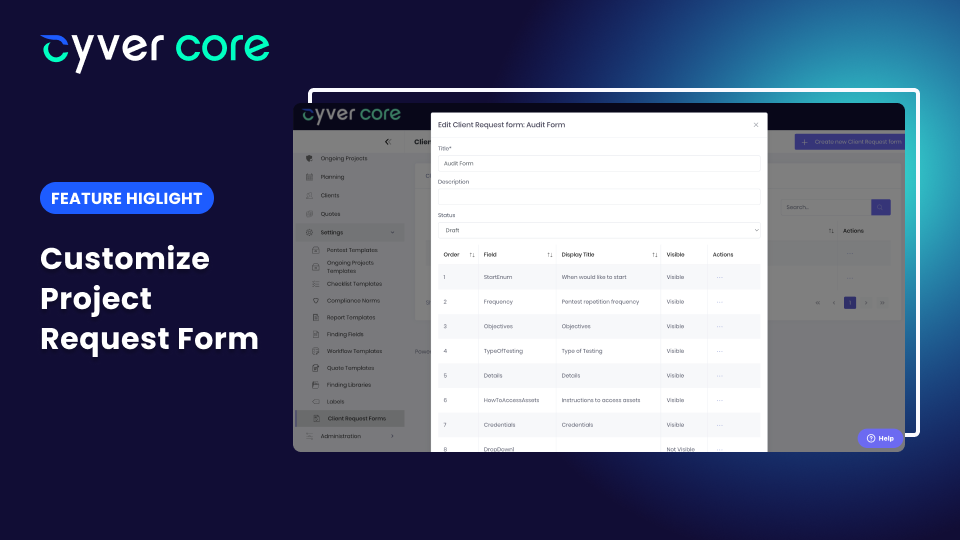
Pentest-as-a-Service delivery means putting project starts in the hands of your clients. The request form in your Cyver Core portal allows your clients to send you a project request, typically based on existing project scope and assets in the portal. That feature...
by Cyver | Sep 1, 2023 | New Features
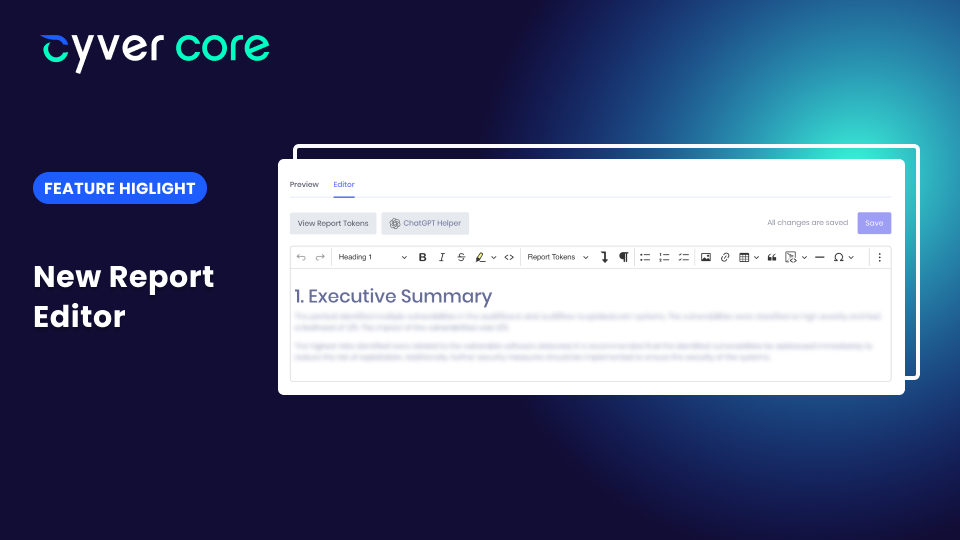
The pentest report is an import deliverable for most pentesters. That’s true whether you’re doing traditional pentesting, red teaming, purple teaming, or vulnerability assessments. Many clients still want the PDF report – even alongside a portal and findings as...
by Cyver | Jul 26, 2023 | New Features
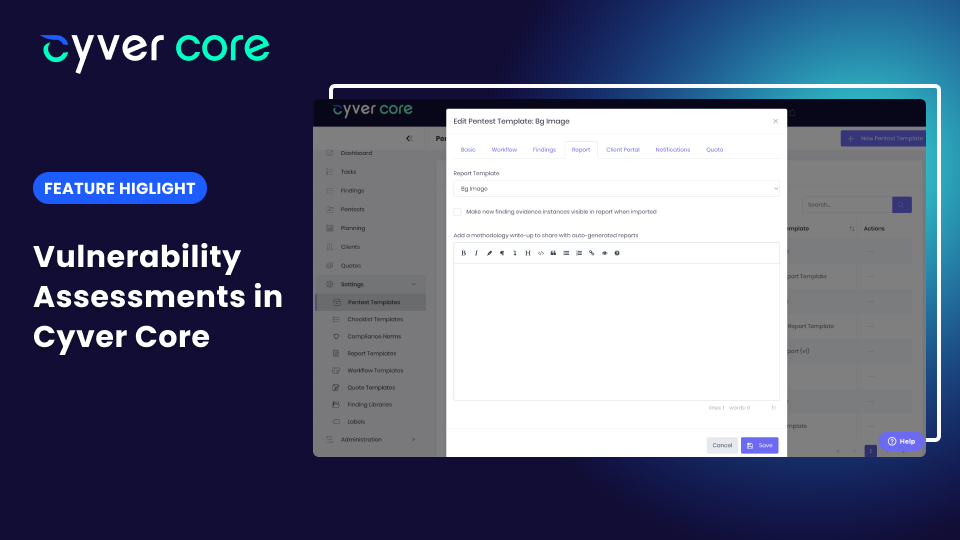
Cyver Core is designed for pentesters and ethical hackers using their skills to help companies improve their cybersecurity profile. So, it makes sense that our users would want to deliver more than just traditional pentesting reports. In fact, vulnerability...
by Cyver | Jun 29, 2023 | New Features
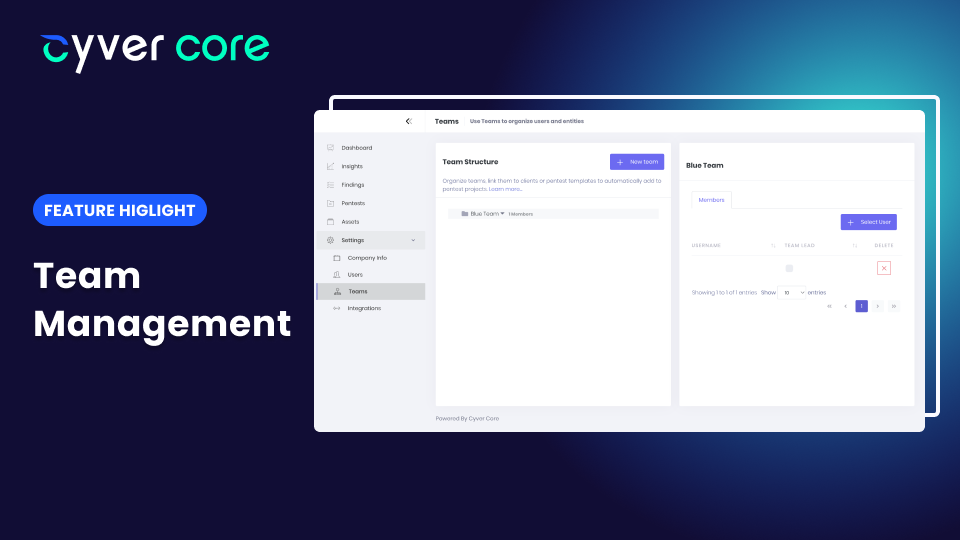
Cyver Core’s pentest management portal allows you to onboard teams and people or pentest firms and their clients. Originally, that team and user access management was restricted to the pentest management portal, putting the pentester in full control of their client...
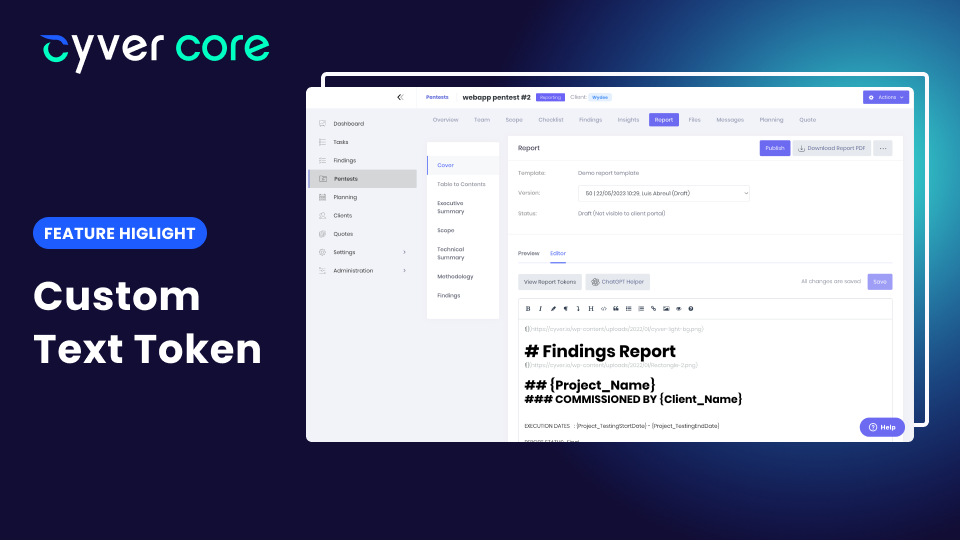
by Cyver | Jun 1, 2023 | New Features
Building the pentest report is one of the most time-consuming parts of pentesting. But, for clients testing for compliance or for those who still want a traditional pentest report, you still need the report. That’s why Cyver Core integrates pentest report generation...






