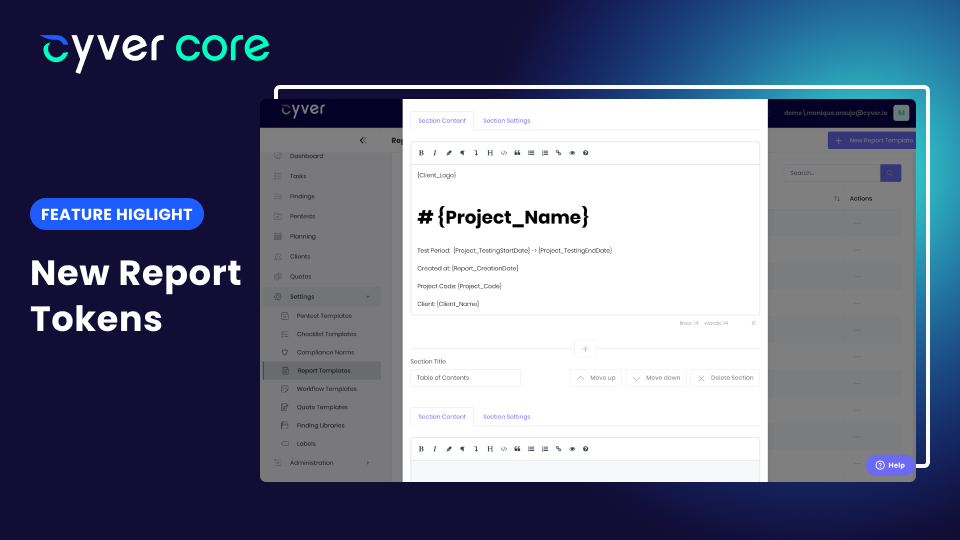
by Cyver | May 10, 2023 | New Features
Cyver Core’s approach to pentest reporting and delivery shifts the focus away from using a pentest report and towards delivering vulnerabilities as tickets. At the same time, many of our users still deliver a full PDF report to clients for compliance reasons and for...
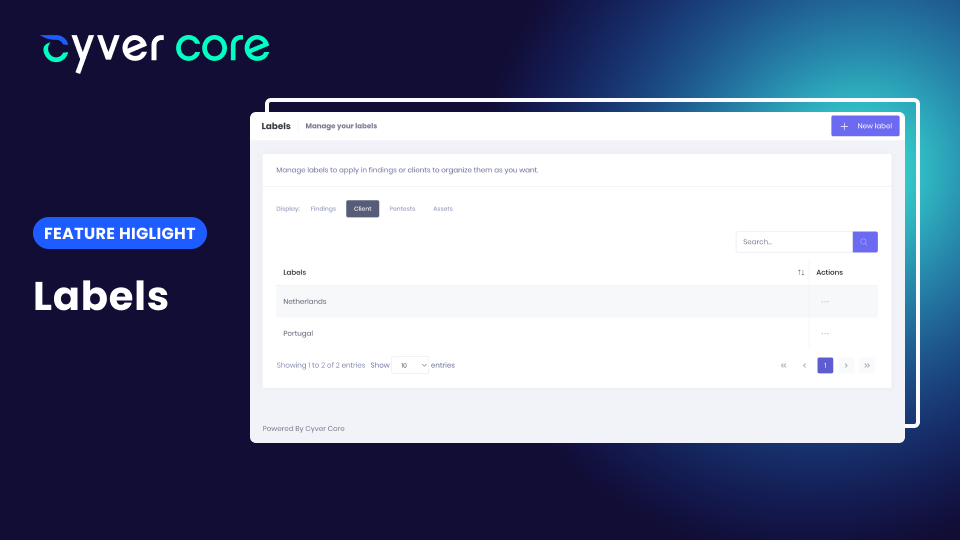
by Cyver | Apr 4, 2023 | New Features
Working with a pentest management platform means you use standardization to enable automation. That’s the same with any cloud platform, from simple Kanban boards like Trello to advanced enterprise resource management like SAP S/4HANA. Having uniform titles, data...

by Cyver | Jan 30, 2023 | New Features
Qualys is a popular vulnerability assessment tool, used by pentesters to find and quantify devices, systems, and vulnerabilities. It also automatically checks for OWASP Top 10 and other well-defined risks, can track vulnerabilities over time, and integrates into IT...

by Cyver | Dec 16, 2022 | New Features
For many pentesters, building a good pentest report is a crucial part of delivering work. While most ethical hacking lies in finding vulnerabilities and attempting to exploit them, clients never see that work. Instead, they rely on deliverables detailing the data you...
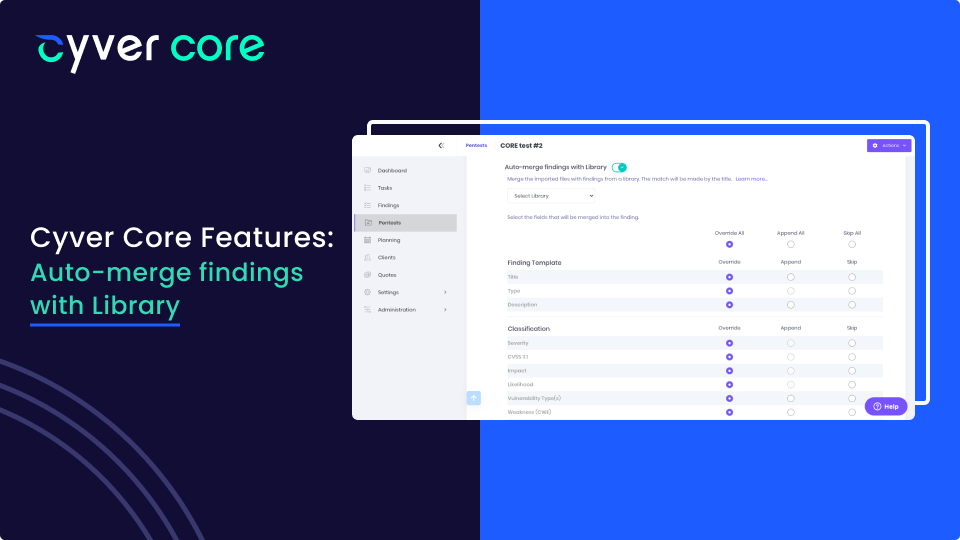
by Cyver | Nov 7, 2022 | New Features
Most pentesters use a vulnerability library to save time when building a report. Here, you normally maintain a collection of descriptions for vulnerabilities you’ve written in the past. Then, when you have a similar vulnerability, you copy-paste that description and...
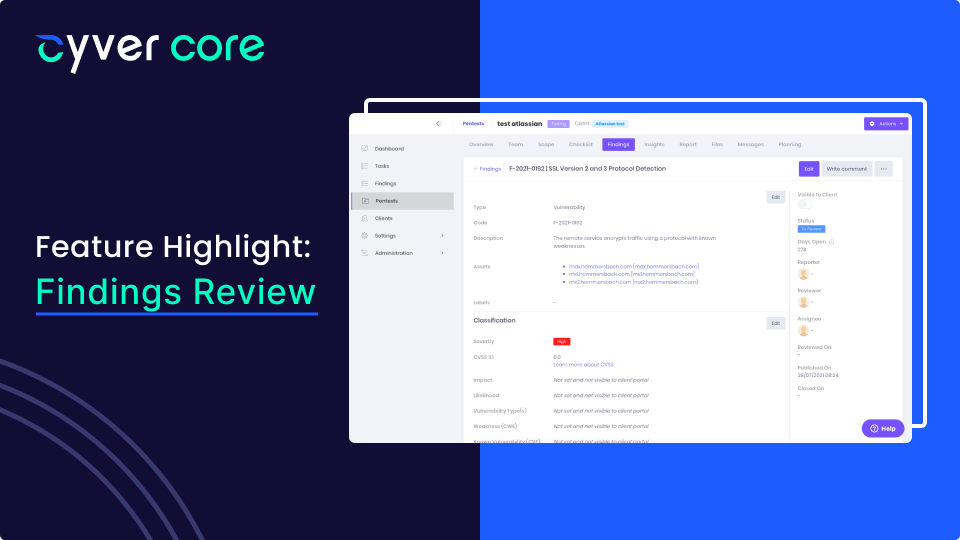
by Cyver | Jul 27, 2022 | New Features
For many organizations, pentesting means relying on either an internal or external team to test assets, look for vulnerabilities, and exploit anything that is found. Working in teams allows ethical hackers to leverage diverse skill sets and insights, with room to...








